OneID interoperability
The way to be interoperable with legacy protocols is to "look" like a centralized IdP. To do this, the OneID repository itself can assert the user's identity in a similar way that traditional IdP works. This is not as secure as the end-to-end secure protocols that OneID recommends, but it has the benefit of compatibility with exising standards.
OpenID Connect
We are writing a Ping Federate adapter. This will enable OneID to be a virtual SAML2 IdP (where a corporation can configure one or more "dedicated" SAML2 IdP and specify which OneID users are members of that virtual IdP) as well as an OpenID Connect IdP.
OpenID 2.0
Downgrading to legacy federation protocols based on identity assertions from traditional centralized models is possible with OneID. This has the advantage of compatibility, but since we are downgrading to a legacy protocol, it is only end to end secure from that IdP to the RP, not from the user to the relying party.
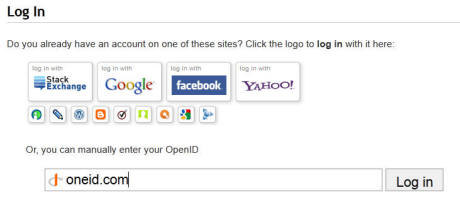
We have an OpenID 2.0 IdP that works with OneID. This will enable you to sign into websites using your OneID by typing "oneid.com" into the OpenID URL box on any website supporting OpenID. If you are already signed into OneID on the browser, this will instantly log you in without further clicks on your part. No username, no password, and a short URL "oneid.com."
You will also be able to create your own virtual OpenID provider, e.g., mysite.oneid.com where you can specify which OneID users you want on that provider so that you can build a site that relies on that provider and easily manage the users who have access to your webservice.
This is not end-to-end secure because OpenID isn't end to end secure, but it does enable OneID to be used at many more websites.
Look for the OpenID URL:
or look for the OpenID tile:
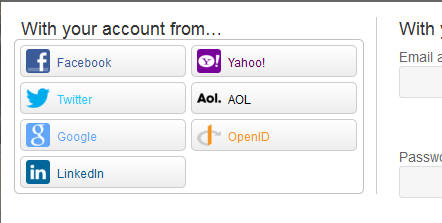
SAML 2.0
We are currently exploring a way for corporations to create a "virtual" SAML server in just a few seconds. You'd go to a webpage, hit a "Create" button, enter the email addresses (no passwords) of people who should be authorized, and you will have an instant SAML 2 server that will only validate identities of the people you entered. You can edit the list at any time (in the future you'll be able to tie it to your LDAP or AD server). Upon creation, you'll be issued your own key pair, cert, and issuer so you can have independence from other virtual server and can enter these parameters into SAML applications. So it acts like your own private SAML server which could be used for SSO into Salesforce and other applications that support SAML 2 logins. But it was extremely easy to set up because everything is done for you. So the SAML interface is similar to the approach with OpenID 2.0 in that we allow you to create your own virtual private IdP.
The approach we are taking is:
-
Make a gateway (IdPproxy) between SAML2 and OneID..
-
Add functionality to the IdPproxy that allows for restricting the use of a specific instance to a specified number of users. Add capability for importing/exporting metadata. Doable from a GUI as well as editing a file.
-
Add functionality that would allow for enhancing the released information about individual users by fetching information from a LDAP/AD service.
Shibboleth
We are working on a plug-in for your existing Shibboleth or Touchstone server. Contact us for details.